1. temp = concat(K4K0, A(K4K0, left(r0)))
2. p0 = r0 XOR temp
3. return p0
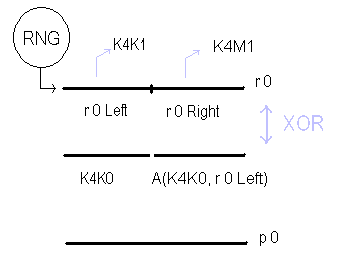
|
Variables: byte[] temp 1. temp = concat(K4K0, A(K4K0, left(r0))) 2. p0 = r0 XOR temp 3. return p0 |
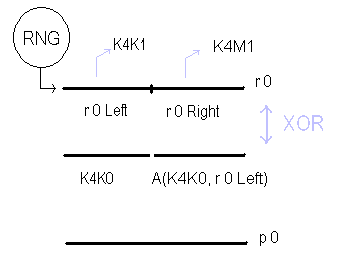
|
|
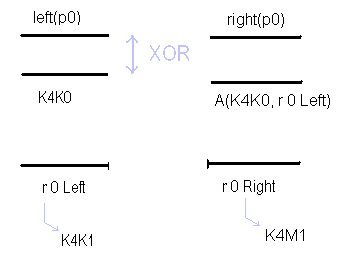
INPUT: byte[] p0, K4K0 (shared) OUTPUT: byte[] r0 Variables: byte[] temp, r0Left, r0Right 1. r0Left = left(p0) XOR K4K0 2. temp = A(r0Left, K4K0) 3. r0Right = right(p0) XOR temp 4. r0 = concat(r0Left, r0Right) 5. return r0 |
|
|
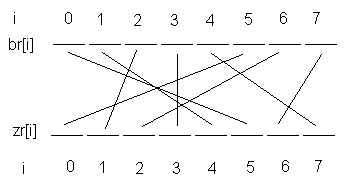
Example: Let nBlock=8, perm = {5, 2, 6, 3, 1, 0, 7, 4}.
The figure graphically shows this permutation. |
|